Section 1: Setting Up Our Virtual Environment
| Course Overview | Return to Section 0 | Proceed to Section 2 |
Section 1: Setting Up Our Virtual Environment

1.1. Introduction
In this section we’ll set up the three VMs we’ll need for the course - Windows 10 (Victim), Kali Linux (Attacker), and Ubuntu 20.04 (Post-Mortem Analysis). First we’ll download the iso images and use them to install the operating systems. Then, depending on the specific VM, we’ll perform some configurations as well as install extra software.
1.2. Requirements
I do want to give you some sense of the hardware requirements for this course, however I also have to add that I am not an expert in this area. AT ALL. So I’ll provide an overview of what we’ll be running, as well as what I think this translates to in terms of host resources (ie your actual system). But please - if you disagree with my estimation and believe you can get the same results by adapting the process, then please do so. After all - this is the way of the hacker.

As mentioned above, we’ll create 3 VMs in total, however, at any one moment there will only be a maximum of 2 VMs running concurrently. For each of these VMs I recommend the following system resources:
- min 2 (ideally 4) CPU cores
- min 4 (ideally 8) GB RAM
- around 60 GB HD space (allocated)
So based on this, that is roughly 2x the above + resources for your actual host system, you would likely need something along the lines of:
- 8 CPU cores (12+ even better)
- 16 GB RAM (32+ even better)
- 200 GB free HD space

Now I understand this requirement is rather beefy, but consider:
- You don’t have to use a single system to run the entire VLAN - you could create an actual physical network, for ex with a Raspberry Pi cluster, and run the VMs on that. Or mini-pcs, or refurbished clients - really for a few hundred dollars you could more than easily be equipped to run a small network. I don’t want to sound insensitive to a few 100 dollars, but I’m gonna level with you:
if you want to learn cybersecurity then there is no better investment than having localized resources to create virtual simulations. - In case you don’t want to invest up-front but don’t mind paying some running costs: You can also use a service like Linode and simply rent compute via the cloud. You can then install your VMs on that, and have access to them for as long as you care to foot the bill.
Finally I want to mention that beyond the hardware, everything we will use is completely free. This course ain’t upselling a full course, and every piece of software is freely available. The sole exception has free alternatives, which I’m about to discuss with you right now.
1.3. Hosted Hypervisor
So in the off-chance you don’t know: a hosted (type 2) hypervisor is the software that allows us to run virtual machines on top of our base operating system. It’s kinda like Inception - it allows us to create systems within our systems.

For this course I’ll be using VMWare Workstation, which as of writing costs around $200. However you could also do it with either VMWare Player, or Oracle Virtualbox, both of which are free.
I’ve used both VMWare Player and VirtualBox in the past, they mostly work well but running into some issues from time-to-time should not be completely unexpected. That being said, the problems I encountered were all, in hindsight, opportunities to learn. Frustrating - feck yesh. Enriching - sure.
Since I switched over to VMWare Workstation my experience has been significantly more stable, so if you do have the money and are committed to this path as a career I would definitely consider getting it. That being said I don’t wanna come across as some corporate shill, so really the choice is totally up to you.
Note that if you decide to not use VMWare Workstation then some of the details of the setup might be different. When that occurs it’ll be up to you to figure out how to adapt it for your situation - Google, ChatGPT, StackExchange, common sense etc. Again, use the opportunities when things don’t happen exactly “as they should” to learn. As a wise emperor once said - The impediment to action advances action. What stands in the way becomes the way.
So at this point please take a moment to download and install the hypervisor of your choice.
Once that’s done with feel free to proceed…

1.4. VM Images
Now that you have your hypervisor up and running the next thing we need to do is install our actual virtual machines. There are a few ways to do this, you can for example simply download the entire VM and simply import it into your hypervisor. This does usually mean that the file you’ll be downloading will be quite large, so we’ll opt for another approach - using iso files. You can think of an iso file simply as a “virtual copy” of the installation disc. So instead of importing the completed VM, we will be installing the VM ourselves using the iso image.
So please go ahead and download the following 3 iso’s:
- For the victim we’ll use Windows 10 Enterprise Evaluation 32-bit. Note that MS will want you to register (it’s free), so do so to download the iso OR click here to go to a Microsoft Tech Community post with direct download links.
- For the attacker we’ll use Kali Linux.
- For post-mortem analysis we’ll be using Ubuntu Linux Focal Fossa. The reason being is in future courses we’ll be using RITA, which, as of writing, runs best on Focal Fossa.
Once you’ve successfully downloaded all three iso images we are ready to proceed.
1.5. VM 1: Windows 10 aka “The Victim”

1.5.1. Installation
- In VMWare Workstation goto
File-> New Virtual Machine. - Choose
Typical (recommended), then clickNext. - Then select
I will install the operating system laterand hitNext.
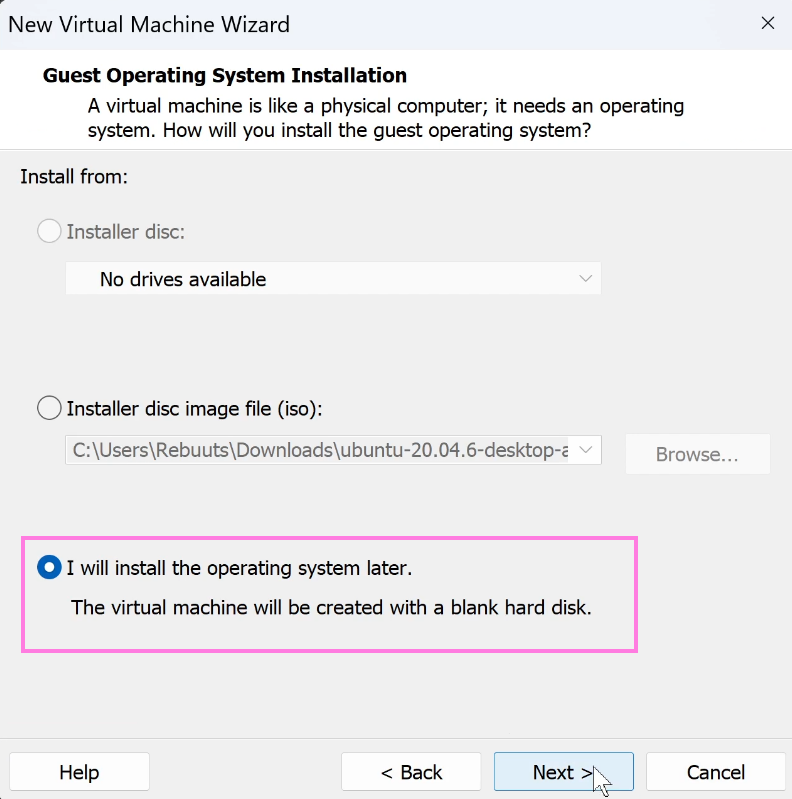
- Select
Microsoft Windows, and under Version selectWindows 10. - Here you are free to call the machine whatever you’d like, in my case I am calling it
Victim. - Select 60 GB and
Split virtual disk into multiple files. - Then on the final screen click on
Customize Hardware.
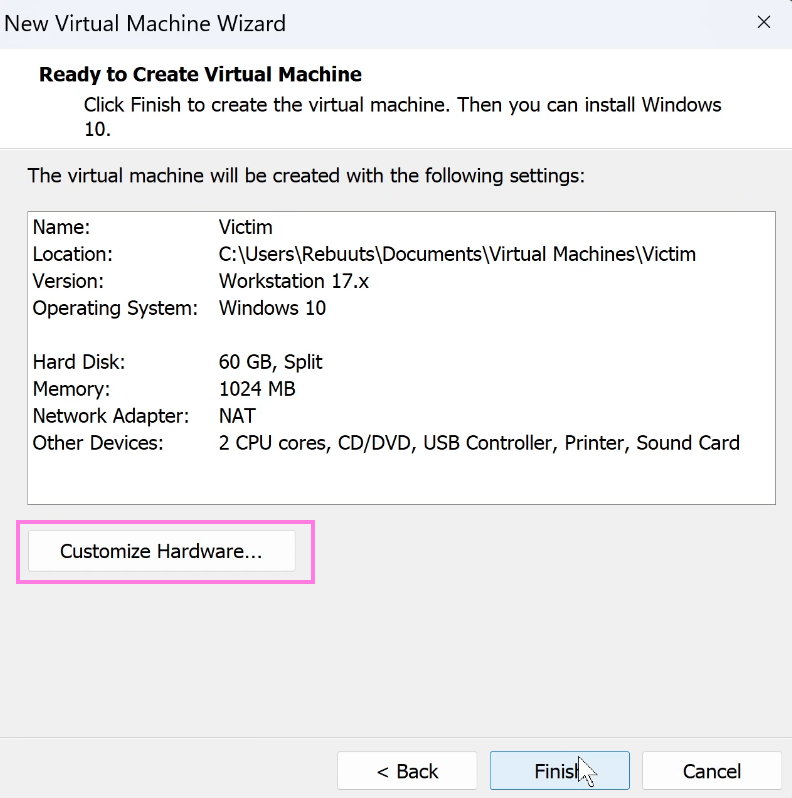
- Under
Memory(see left hand column) I suggest at least 4096 MB, if possible given your available resources then increase it to 8192 MB. - Under
ProcessorsI suggest at least 2, if possible given your available resources then increase it to 4. - Under
New CD/DVD (SATA)change Connection from Use Physical Drive toUse ISO image file. ClickBrowse…and select the location of your Windows 10 iso file. - Once done click
Closeon the bottom to exit out of the Hardware options dialog box. - Select
Finish.
You should now see your VM in your Library (left hand column), select it and then click on Power on this virtual machine. If you don’t see a Library column on the left simply hit F9 which toggles its visibility.
Wait a short while and then you should see a Windows Setup window. Choose your desired language et cetera, select Next and then click on Install Now. Select I accept the license terms and click Next. Next select Custom: Install Windows only (advanced), and then select your virtual HD and click Next.
Once its done installing we’ll get to the setup, select your region, preferred keyboard layout etc. Accept the License Agreement (if you dare - mwhahaha!). Now once you reach the Sign in page don’t fill anything in, rather select Domain join instead in the bottom left-hand corner.
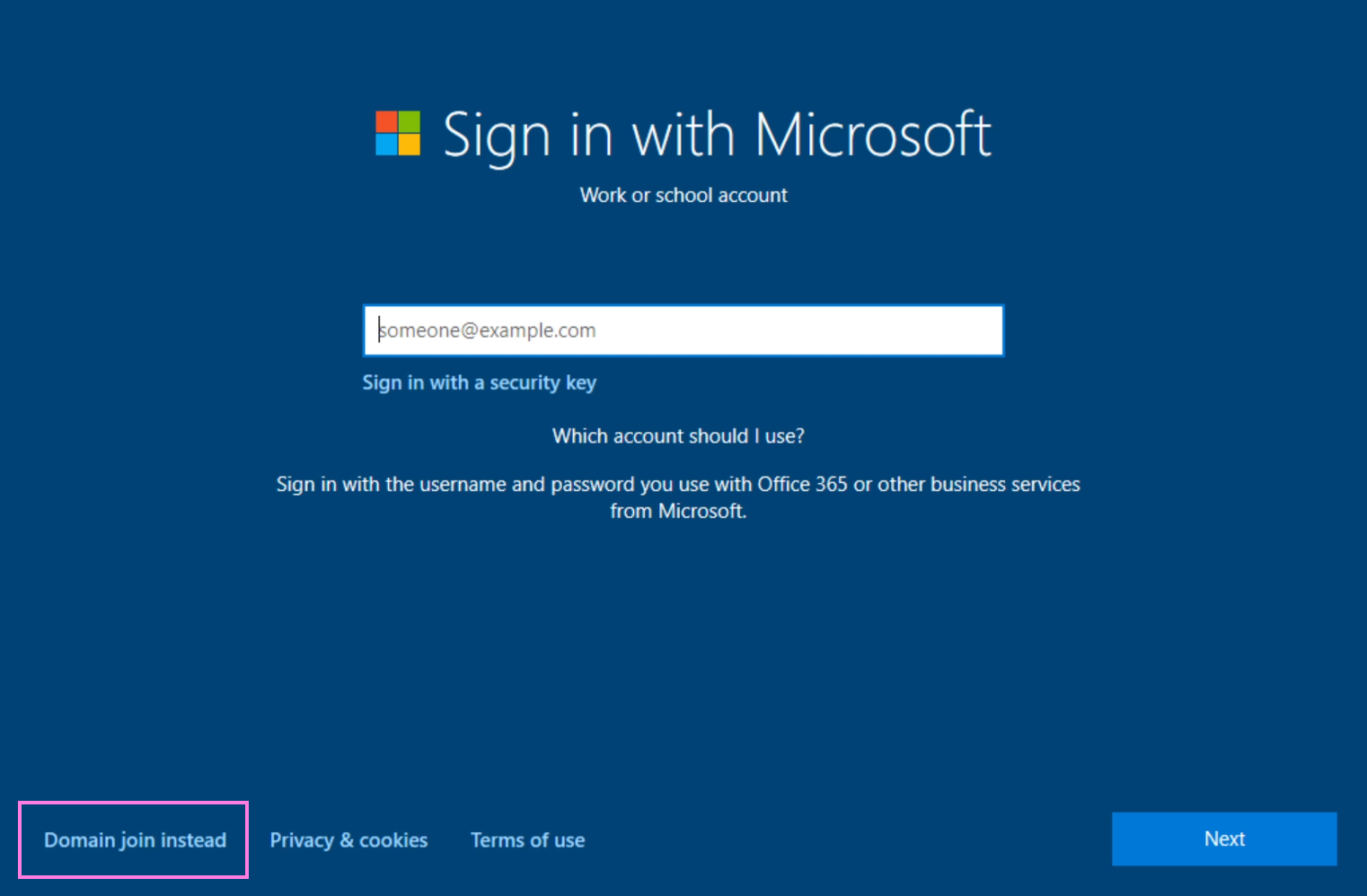
Choose any username and password, in my case it’ll be the highly original choice of User and password. Then choose 3 security questions, since this is a “burner” system used for the express purpose of this course don’t overthink it - randomly hitting the keyboard a few times will do just fine. Turn off all the privacy settings, and for Cortana select Not Now.
Windows will now finalize installation + configuration, this could take a few minutes, whereafter you will see your desktop.
1.5.2. VMWare Tools
Next we’ll install VMWare Tools which for our purposes does two things. First, it ensure that our VMs screen resolution assumes that of our actual monitor, but more importantly it also gives us the ability to copy and paste between the host and the VM.
So just to be sure, at this point you should be staring at a Windows desktop. Now in the VMWare menu bar click VM and then Install VMWare Tools. If you open Explorer (in the VM) you should now see a D: drive.
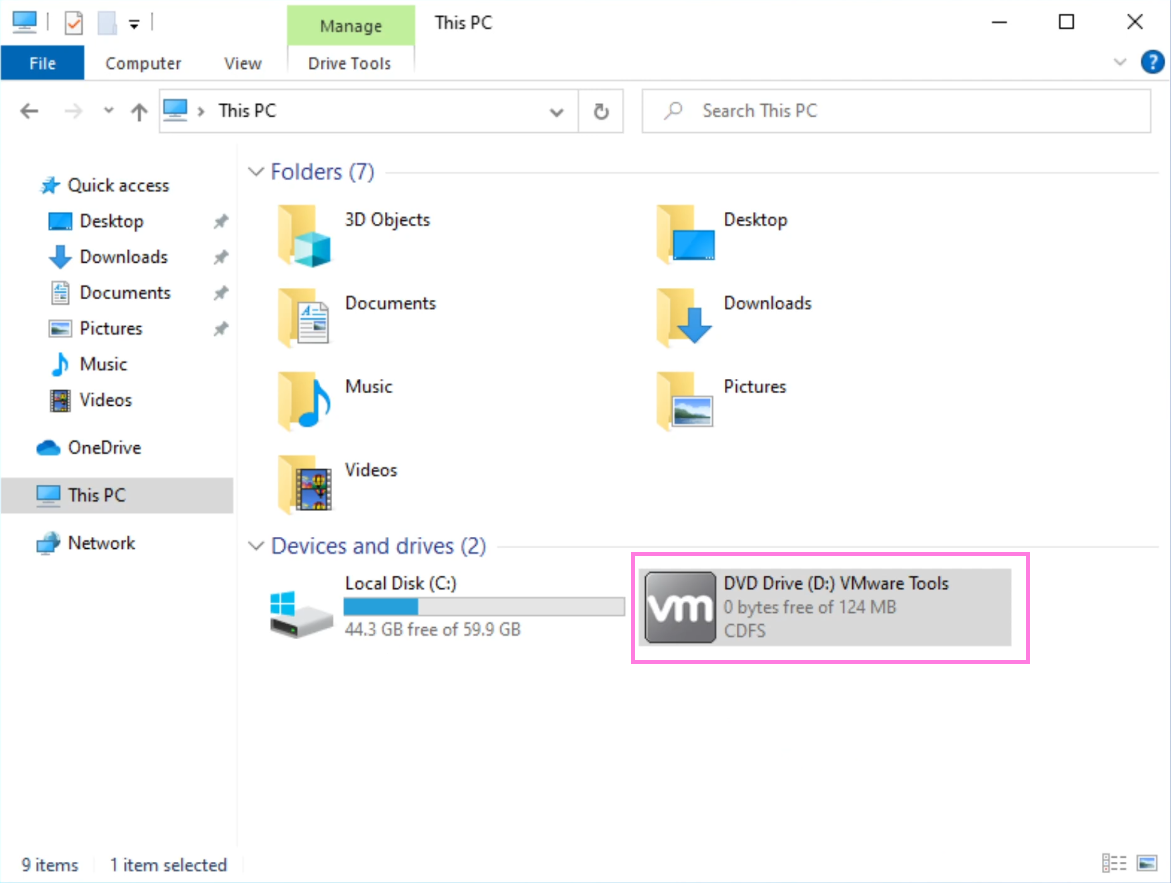
Double-click the drive, hit Yes when asked if we want this app to make changes to the device. Hit Next, select Typical and hit Next. Finally hit Install and then once done Finish. You’ll need to restart your system for the changes to take effect, but we’ll shut it down since we need to change a setting. So hit the Windows icon, Power icon, and then select Shut Down.
Right-click on your VM and select Settings. In the list on the LHS select Display, which should be right at the bottom. On the bottom - deselect Automatically adjust user interface size in the virtual machine, as well as Stretch mode, it should now look like this:
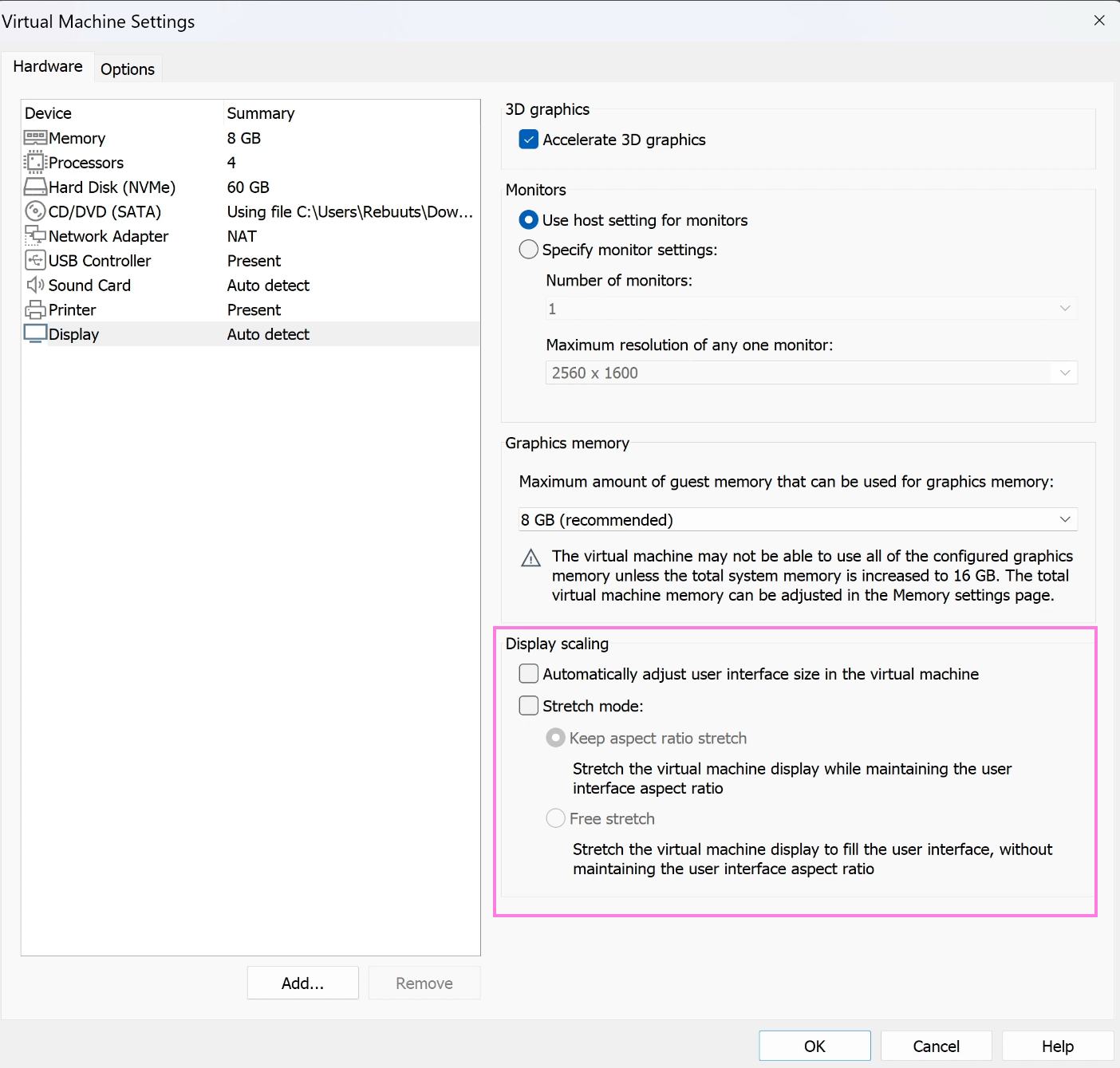
Go ahead and start-up the VM once again, we’ll now get to configuring our VM.
1.5.3. Deep disable MS Defender + Updates
I call this ‘deep disable’ because simply toggling off the switches in Settings won’t actually fully disable Defender and Updates. You see, Windows thinks of you as a younger sibling - it feels the need to protect you a bit, most of the time without you even knowing. (Unlike Linux of course which will allow you to basically nuke your OS kernel if you so desired.)
And just so you know why it is we’re doing this…
We are disabling Defender so that the AV won’t interfere with us attacking the system. Now you might think well this represents an unrealistic situation since in real-life we’ll always have our AV running. Thing is, this is a simulation - we are simulating an actual attack.
Yes, the AV might pick up on our mischievous escapades here since we are using a well-known and widely-used malware framework. But, if you are being attacked by an actual threat actor worth their salt they likely won’t be using something so common. It’s not that much of a stretch to assume they will be capable of using analogous technologies that our AV will not pick up on. Thus, by turning off Defender this is what we are simulating.
And as for updates, we disable this because sometimes we can spend all this time configuring and setting things up and then one day we boot up our VM up, Windows does it’s whole automatic update schpiel, and suddenly things are broken. This is thus a small time investment to hedge against extreme potential frustration. So worth it.

Disable Tamper Protection
- Hit the
Starticon, then select theSettingsicon. - Select
Update & Security. - In LHS column, select
Windows Security, then clickOpen Windows Security. - A new window will pop up. Click on
Virus & threat protection. - Scroll down to the heading that says
Virus & threat protection settingsand click onManage settings. - There should be 4 toggles in total, we are really interested in disabling
Real-time protection, however since we are here just go ahead and disable all of them. - Note that Windows will warn you and ask if you want to allow this app to make changes to the device, hit
Yes. - All 4 toggle settings should now be disabled.
- Hit the
Disable the Windows Update service
- Open the Run dialog box by pressing Win+R.
- Type
services.mscand press Enter. - In the Services list, find
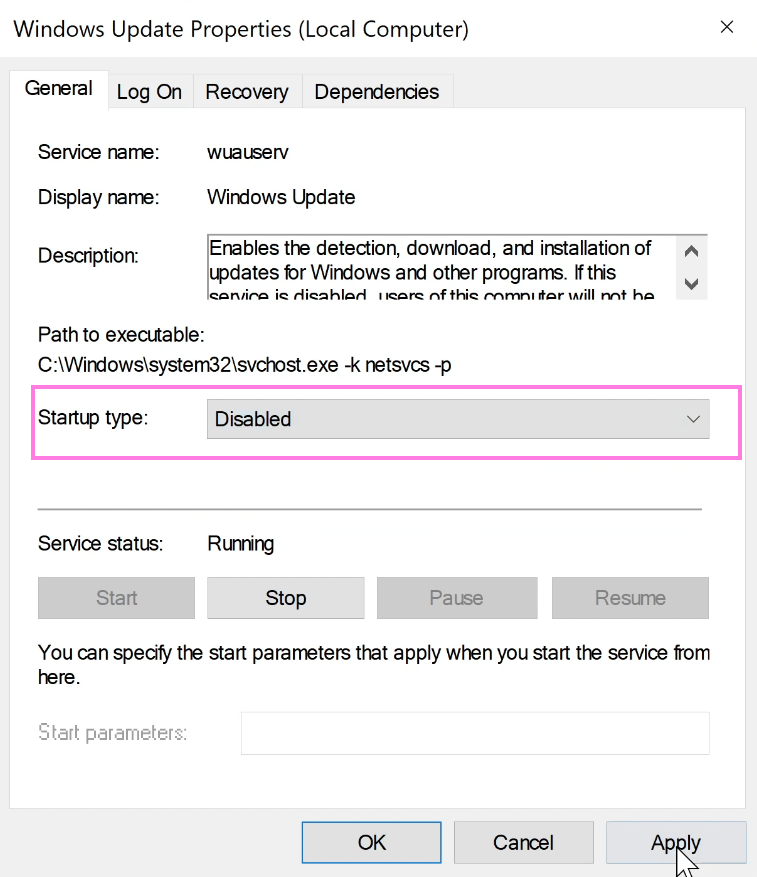
Windows Update, and double-click it. - In the Windows Update Properties (Local Computer) window, under the
Generaltab, in theStartup type:dropdown menu, selectDisabled- see image below. - Click
Applyand thenOK.
- Disable Defender via Group Policy Editor
- Open the Run dialog box by pressing Win+R.
- Type
gpedit.mscand hit enter. TheLocal Group Policy Editorshould have popped up. - In the tree on the LHS navigate to the following:
Computer Configuration>Administrative Templates>Windows Components>Microsoft Defender Antivirus. - In the RHS double-click on
Turn off Microsoft Defender Antivirus. - In the new window on the top left select
Enabled- see image below. - First hit
ApplythenOK.
Disable Updates via Group Policy Editor
- Still in
Local Group Policy Editor, navigate to:Computer Configuration>Administrative Templates>Windows Components>Windows Update. - In the RHS double-click on
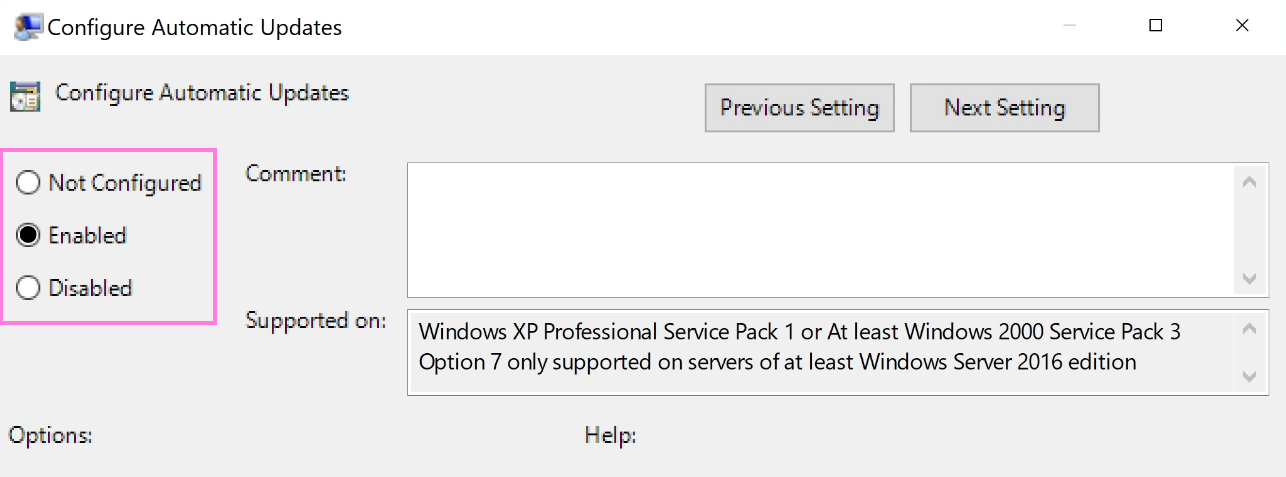
Configure Automatic Updates. - Select
Disabled, then clickApplyandOK.
- Still in
Disable Defender via Registry
- In the search bar on the bottom type
cmd. - On the top left, right under
Best matchyou should seeCommand Prompt. - Right-click and select
Run as administrator, hitYes. - Copy and paste the following command below into your command prompt and hit enter.
REG ADD "hklm\software\policies\microsoft\windows defender" /v DisableAntiSpyware /t REG_DWORD /d 1 /f- In the search bar on the bottom type
Almost there! We just need to boot into Safe Mode to make some final adjustments to the registry and then we are good to go.
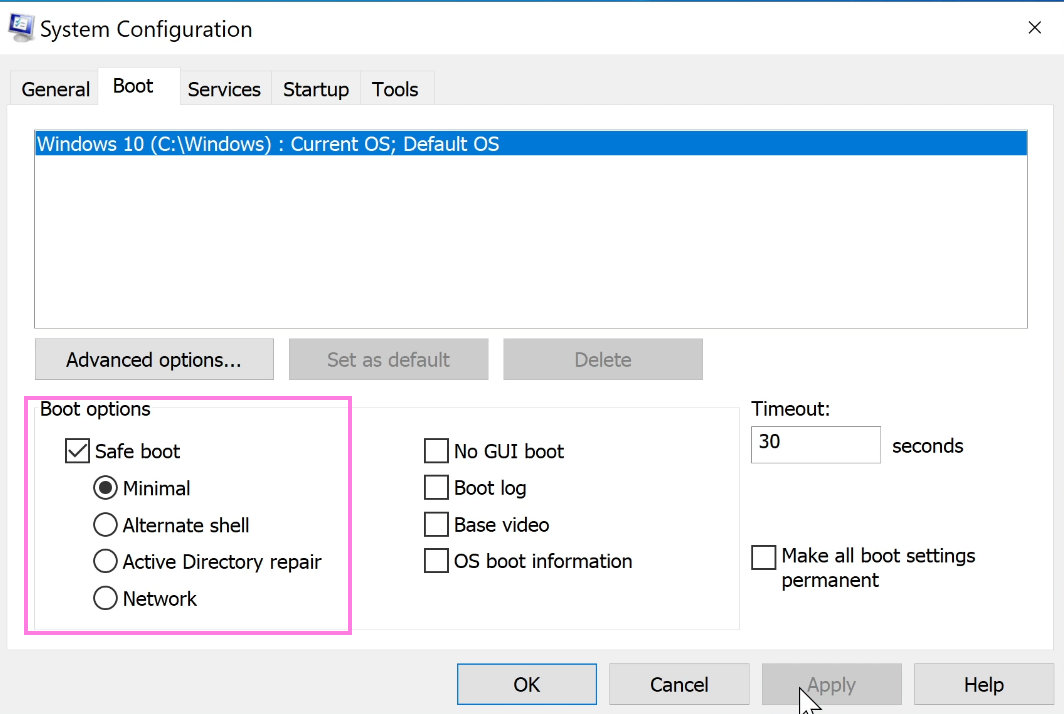
- Reboot system in Safe Mode
- Open the
Rundialog box by pressing Win+R. - Write
msconfigand hit enter. - Select the
Boottab. - Under
Boot optionsselectSafe boot, ensureMinimalis selected - see image below. - Hit
Applyfirst, theOK. - Select
Restart.
- Open the
Once your system has restarted in Safe mode…
- Disable Defender via Registry
- Open the
Rundialog box by pressing Win+R. - Write
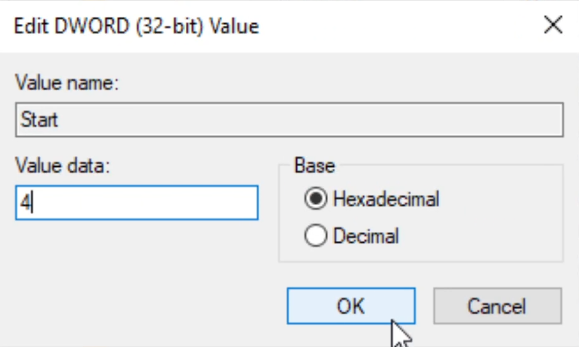
regeditand hit enter, this should bring up theRegistry Editor. - Below you will see a list of 6 keys. For each of these keys you will follow the same process: once the key is selected find the
Startvalue in the RHS, double-click, change the value to4and hitOK- see image below.
Computer>HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>Services>SenseComputer>HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>Services>WdBootComputer>HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>Services>WinDefendComputer>HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>Services>WdNisDrvComputer>HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>Services>WdNisSvcComputer>HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>Services>WdFilter
- Open the
Disable Updates via Registry
- Still in
Registry Editorlet’s navigate to the following:
Computer>HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows>CurrentVersion>WindowsUpdate>Auto Update
- Right-click the
Auto Updatekey, selectNew, and then clickDWORD (32-bit) Value. - Name the new key
AUOptionsand press Enter. - Double-click the new
AUOptionskey and change its value to2. ClickOK. - Close Registry Editor.
- Still in
Leave Safe Mode
- All that’s left to do is get back into our regular Windows environment.
- Open the
Rundialog box by pressing Win+R. - Write
msconfigand hit enter. - Select
Boottab. - Deselect
Safe boot, hitApply, hitOK. - Hit
Restart.
And that, I can promise you, is by far the most boring part of this entire course. But the good news is that this is potentially the last time you have to do it. Ever. This is because we can now convert this VM to a template and clone it indefinitely in the future.
But before we learn to do that, let’s setup all the awesome tools we’ll be using in this course.
1.5.4. Sysmon
You should now be back in the normal Windows environment looking at your desktop. Let’s set up Sysmon - a simple, free, Microsoft-owned program that will dramatically improve our logging ability.

Before we install Sysmon there’s just one thing you need to know - in addition to downloading Sysmon itself, we also need a config file. One day when you get to that level you can even create your own config file, which will allow you to make it behave exactly how you want it to.
But for now, since we are decidedly not yet there, let’s download and use one made by some really smart people. Of late I have heard a few trusted sources, included Eric Conrad prefer this version from Neo23x0 whose authors included another blue team giant, Florian Roth.
So first download the config file, then go here to download Sysmon. You should now have two zip files - the config you downloaded from Github, as well as the Sysmon zip file. Extract the Sysmon archive, the contents should look as follows:
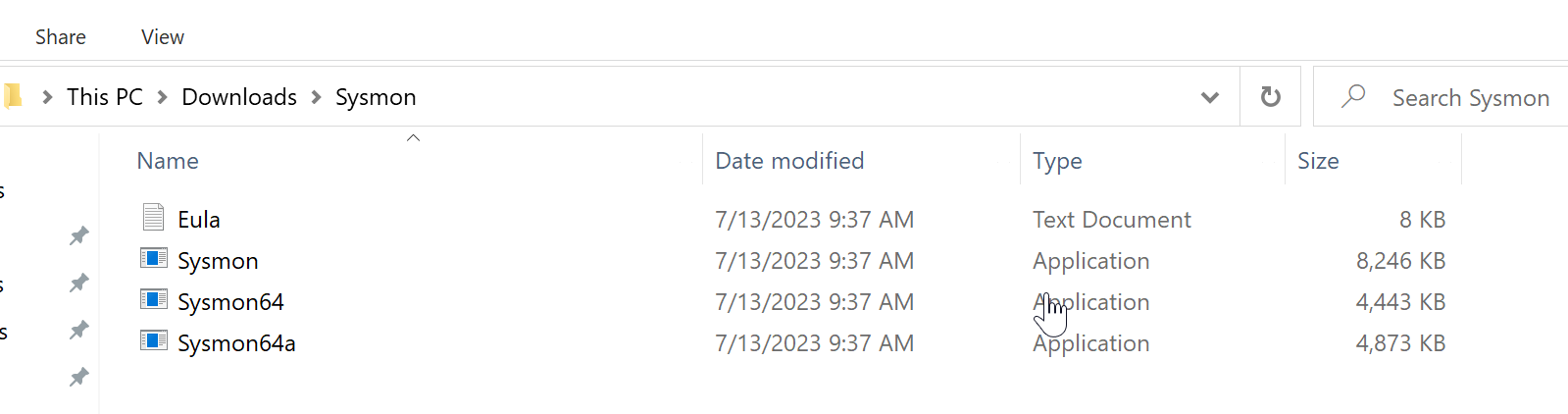
Now also extract the zip file containing the config. Inside of the folder rename sysmonconfig-export.xml to sysmonconfig.xml. Now simply cut (or copy) the file and paste it in the folder containing Sysmon.
Great, everything is set up so now we can install it with a simple command. Open command prompt as administrator and navigate to the folder containing Sysmon and the config file - in my case it is c:\Users\User\Downloads\Sysmon. Run the following command:
Sysmon.exe -accepteula -i .\sysmonconfig.xml
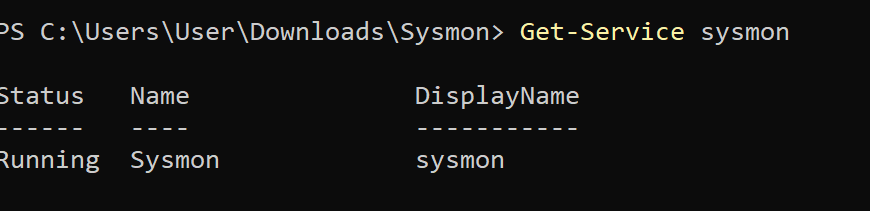
This is what a successful installation will look like:
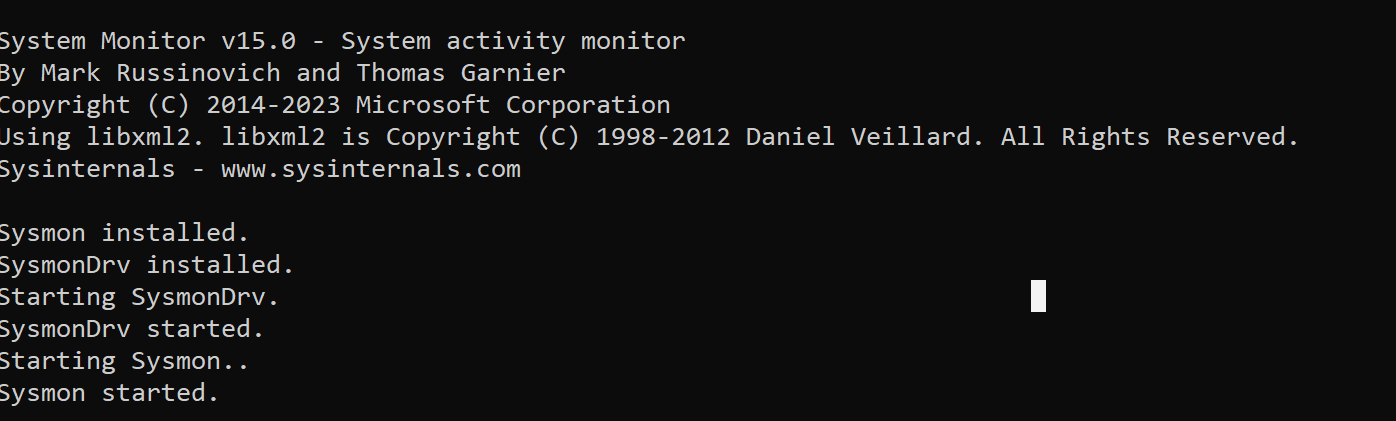
Now let’s just validate that it’s running. In the command prompt run the command powershell so we change over into a PS shell. Then, run the command Get-Service sysmon. In the image below we can see it is running - we are good to go!
That’s it for Sysmon, now let’s enable PowerShell ScriptBlock logging.
1.5.5. PowerShell ScriptBlock Logging
For security purposes, another quick and easy switch we can flip is enabling PowerShell logging. This is great because one specific type of PowerShell logs (ScriptBlock) will record exactly what command was run in PowerShell. As we know, in-line with the Living off the Land paradigm, modern adversaries LOVE abusing PowerShell. It should this be clear why having logs of commands that were run in PowerShell could potentially be of huge benefit to us.
Something to be aware of is that there are a few types of PowerShell logging: Module, ScriptBlock, Operational, Transcription, Core, and Protected Event. For the purposes of this course we will be activating ScriptBlock, as well as Operational. While activating the former tells PowerShell to log the commands, we also need to activate Operational so that the system is able to properly save the logs.
NOTE: This entire process could be performed in the GUI using Group Policy Editor, we will however be performing it via PowerShell command line. You should always prefer this method to using the GUI when it comes to enabling logs. Not simply to look cool, nay, there is a very good practical reason for this.

Imagine for a moment you needed to activate this feature on 1000 stations. You could either do so by logging into each station individually and interacting with the gpedit GUI interface, which would likely take you a few days working at a ferocious pace for all 1000 stations. Alternatively, you could run a single command from a domain controller, which would take less than a minute for any amount of stations.
This is an admittedly dramatic way of saying that performing administrative tasks using PowerShell commands scales well, while flipping GUI toggles does not scale at all. So invest your time early on learning the methods that won’t break down the moment you need to do it at scale, it’s so worth it.

Open PowerShell as an administrator:
- First we’ll set the execution policy to allow us to make the changes:
Set-ExecutionPolicy -ExecutionPolicy Bypass -Scope LocalMachine
- We’ll now create a new registry path for
ScriptBlockLogging:
New-Item -Path HKLM:\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging -Force
- Now create a new DWORD property EnableScriptBlockLogging and set its value to 1:
New-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging -Name EnableScriptBlockLogging -Value 1 -PropertyType DWord -Force
- And finally we’ll enable Operational logging to ensure our ScriptBlock logs are saved properly:
wevtutil sl "Microsoft-Windows-PowerShell/Operational" /e:true
1.5.6. Install Software
And now we’ll install three programs:
- We’ll use Process Hacker for live memory forensics.
- We’ll use winpmem to create a memory dump for post-mortem memory forensics.
- We’ll use Wireshark to generate a pcap for traffic analysis.
You can download Process Hacker here. Once downloaded go ahead and install it.
You can download the latest release of winpmem here. Since its a portable executable there is no installation required, just download the .exe file and place it on the desktop.
And finally the WireShark setup file can be downloaded from here. Once downloaded run setup, just keep all options per default, nothing fancy required.
That’s it friend. We are done with BY FAR the heaviest lifting in terms of VM setup - the remaining two will comparatively be a breeze. But before we get to that there’s one very simple thing we can do that will make our lives much easier in the future - turning this VM into a template for cloning.
1.5.7. Creating a Template
So why do we want to do this again? Well by turning this VM we just created into a template we are in essence creating an archetype (blueprint). Then, whenever we want this same “victim” system for any project or course we can simply clone it as many times as we want.

Thus instead of repeating this entire, rather cumbersome process we can click a few buttons and have it ready to go in a few seconds. This is also useful if we ever “mess up” the VM, we can just come back to this starting point.
So just follow along with these few simple steps:
- First shut down the VM.
- In VMWare you should see the library pane on the LHS listing our VM. If you don’t, hit
F9, or go toView>Customize>Library. - Right-click on our VM (
Victim), selectSnapshot>Take Snapshot. - Name it anything you’d like, I will be calling it
Genesis. HitTake Snapshot. - Again right-click the VM and select
Settings. - On the top left we can see two tabs -
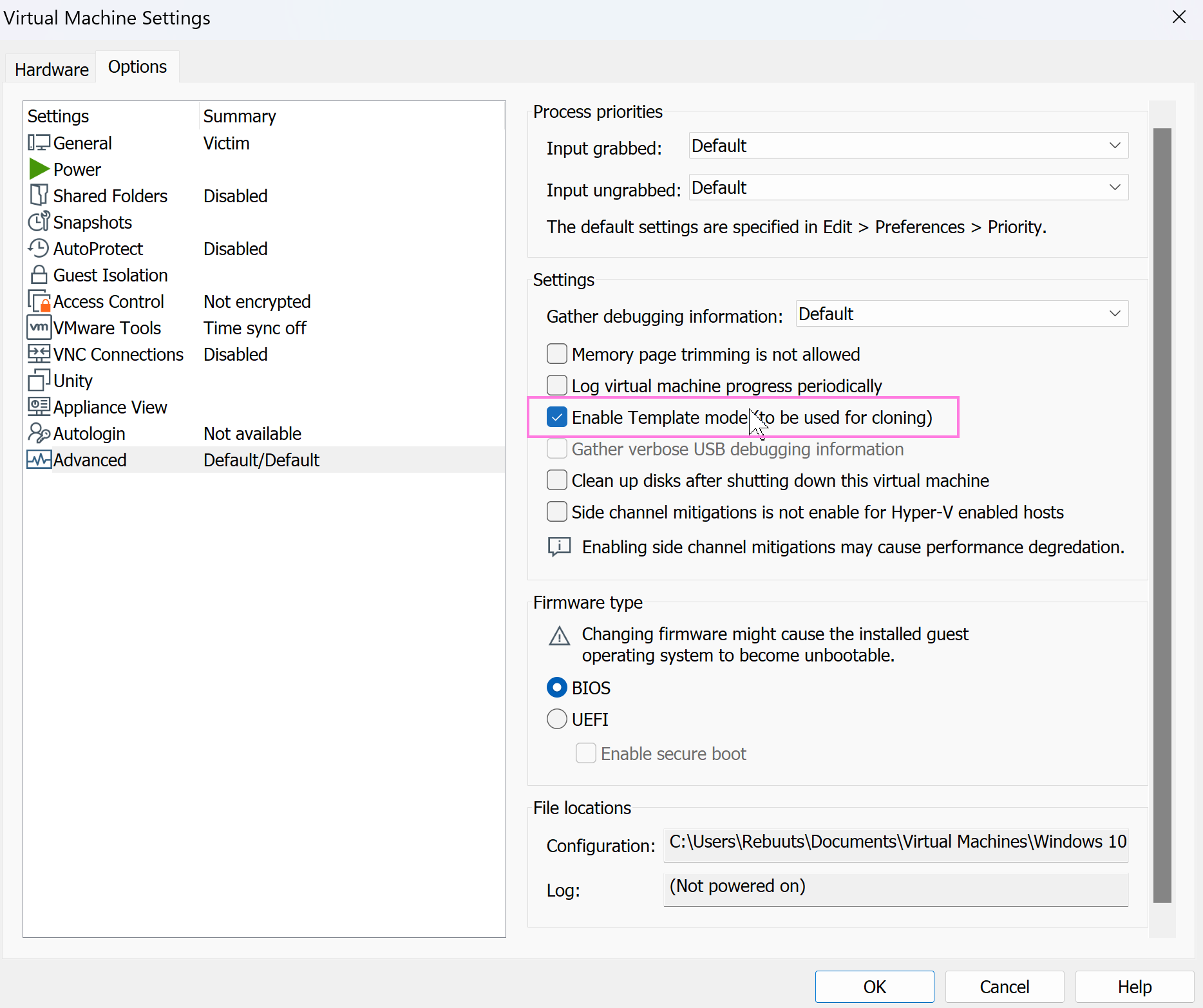
HardwareandOptions, selectOptions. - Go down to the bottom and select
Advanced. - Select
Enable Template mode (to be used for cloning), hitOK.
- Note you might want to rename this VM to something like
Victim Template, so we are aware this is the template that we should not be using, but rather use for cloning. You can do this underSettings>Options>General. - Now let’s create our first clone which we will actually be using in the course. Right-click on
Victim Template, selectManage>Clone. HitNext. - We’ll select the snapshot we created and hit
Next. - Keep selection as
Create a linked cloneand hitNext. - Give your clone a name, I will be calling it
Victim01. Choose a location and hitNext.
That’s it! You should now see both Victim Template and Victim01 in your library.
The bad news - we still have two VMs to install. The good news - they will require minimal-to-no configuration, so at this point we’re about 80% done with our VM setup. So let’s get it done.
1.6. VM 2: Kali Linux aka “The Attacker”

We’ll be using Kali Linux to simulate the attacker. The great thing about Kali Linux is that everything we’ll need comes pre-packaged, so we just have to install the actual operating system.
- In VMWare hit
File>New Virtual Machine... Typical (recommended)and hitNext.I will install the operating system laterand hitNext.- Select
Linux, and under Version selectDebian 11.x 64-bit. (Note: Kali Linux is built on top of Debian Linux). - Again call the machine whatever you’d like, in my case I am calling it
Hacker. - Increase the Maximum disk size to 60 GB and select
Split virtual disk into multiple files. - Then on the final screen click on
Customize Hardware. - Under
MemoryI suggest at least 4096 MB, if possible given your available resources then increase it to 8192 MB. - Under
ProcessorsI suggest at least 2, if possible given your available resources then increase it to 4. - Under
New CD/DVD (SATA)change Connection from Use Physical Drive toUse ISO image file. ClickBrowse…and select the location of your Kali Linux iso image.
So now let’s get to actually installing it:
- Right-click on the VM and select
Power>Start Up Guest. - Select
Graphical Install. - Select language, country etc.
- Choose any
Hostname, leaveDomain nameblank, for Full name and username I chosehacker. - Create a password, again though OBVIOUSLY not a suggested real-world practice, in these simulations I tend to simply use
passwordsince it minimizes any operational friction. - Choose a timezone.
- Next select
Guided - use entire diskand hitContinue. - The only disk should be selected, hit
Continue. - Keep
All files in one partition (recommended for new users), hitContinue. - Keep
Finish partitioning and write changes to disk, hitContinue. - Select
YesandContinue. - In
Software selectionkeep the default selection and hitContinue. Kali will now start installing, just be aware this can take a few minutes, probably around 5 to 10. - Next it’ll ask you about installing a GRUB boot loader, keep it selected as
Yesand hitContinue. - Select
/dev/sdaand hitContinue. More installing… - Finally it will inform us it’s complete, we can hit
Continuecausing the system to reboot into Kali Linux. Enter your username and password and hitLog In. - Let’s shut down the VM, then right-click on it in the library and select
Settings. UnderDisplaydeselectStretch modeand hitOK.
And that’s it for our attacker machine - feel free to repeat the Template-Cloning process we performed for our Windows 10 VM if you so desire.
1.7. VM 3: Ubuntu Linux 20.04 aka “The Analyst”
1.7.1. Installation
And now finally we’ll set up our Ubuntu VM.
- In VMWare hit
File>New Virtual Machine... Typical (recommended)and hitNext.I will install the operating system laterand hitNext.- Select
Linux, and under Version selectUbuntu 64-bit. - Again call the machine whatever you’d like, in my case I am calling it
Analyst. - Increase the Maximum disk size to 60 GB and select
Split virtual disk into multiple files. - Then on the final screen click on
Customize Hardware. - Under
MemoryI suggest at least 4096 MB, if possible given your available resources then increase it to 8192 MB. - Under
ProcessorsI suggest at least 2, if possible given your available resources then increase it to 4. - Under
New CD/DVD (SATA)change Connection from Use Physical Drive toUse ISO image file. ClickBrowse…and select the location of your Ubuntu Linux 20.04 iso image. Make sureConnect at power onis enabled. ClickClosethenFinish.

So now let’s install Focal Fossa:
- Right-click on the VM and select
Power>Start Up Guest. - Select
Try or Install Ubuntu. - Once it boots up the GUI, select
Install Ubuntu. - Select your keyboard and language, hit
Continue. - Keep
Normal Installationselected, deselectDownload updates while installing Ubuntu. - Keep
Erase disk and install Ubuntuselected, then hitInstall Now. - For the popup asking if you want to
Write the changes to disks?, hitContinue. - Choose a timezone and hit
Continue. - Now fill in your name and desired credentials, I’ll be using
analystandpassword. - When it’s complete you can power the system off. Go into settings, under
CD/DVD (SATA)disableConnect at power on. - Then goto
Display, disableStretch mode. - Hit
OK, start the VM up once again, and log in.
NOTE: A few moments after logging in and answer Ubuntu's questions you'll be asked whether you want to upgrade. IMPORTANT: Do not do so, decline the offer.
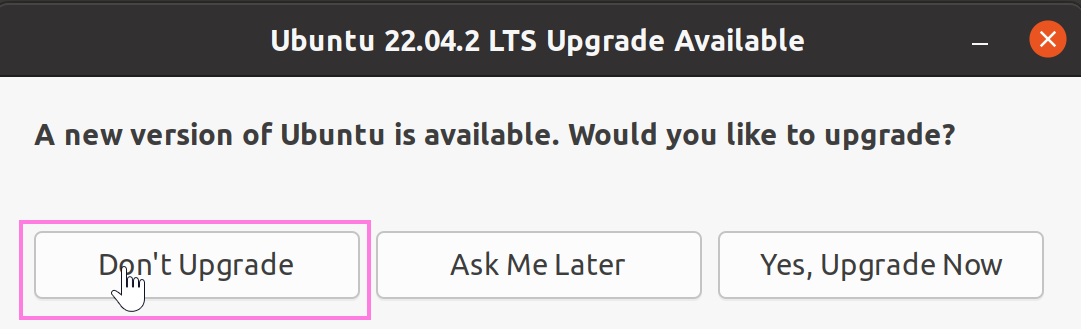
OK, that’s it for the installation, now let’s install the two programs we’ll use in this course.
1.7.2. Install Software
Volatility3
- Either download the zip file from the repo here, or run the command below from terminal to clone the repo:
git clone https://github.com/volatilityfoundation/volatility3.git
- Next we’ll need to install pip, which is a package manager for Python (Volatility is written in Python). We’ll do this so we can install all the required package dependencies. Run the following commands:
sudo apt update
sudo apt install python3-pip
- Once that’s complete we can install our package dependencies. Open a terminal and navigate to where you cloned Volatility. Now simply run the following command:
pip3 install -r requirements.txt
WireShark
- Run the following command to update the packet repository cache:
sudo apt update
- Now run the following command to install WireShark:
sudo apt install wireshark
OK. Do you know what time it is?
Yeah it’s time for all this installing and configuring to pay off - let’s kick things off by performing the attack!

| Course Overview | Return to Section 0 | Proceed to Section 2 |